Confirmed working with
Retrieve Root Password
Method courtesy Of Paul Banks here and here
Pry the device open, there are 8 clips around the edges.
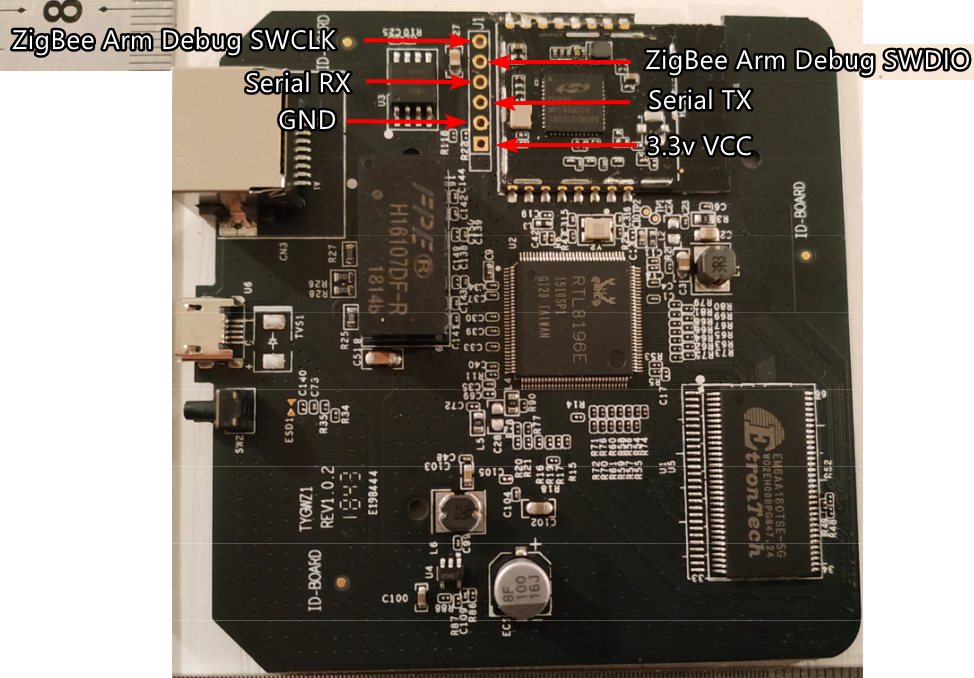
| Gateway | Adapter |
|---|---|
| Serial TX | RX |
| Serial RX | TX |
| GND | GND |
| 3.3v VCC | 3V3/VCC |
Leave the USB Power and 3.3v disconnected.
Open a serial terminal to your TTL with the following settings:
| Setting | Value |
|---|---|
| Baud Rate | 38400 |
| Data Bits | 8 |
| Stop Bits | 1 |
| Parity | None |
| Flow Control | None |
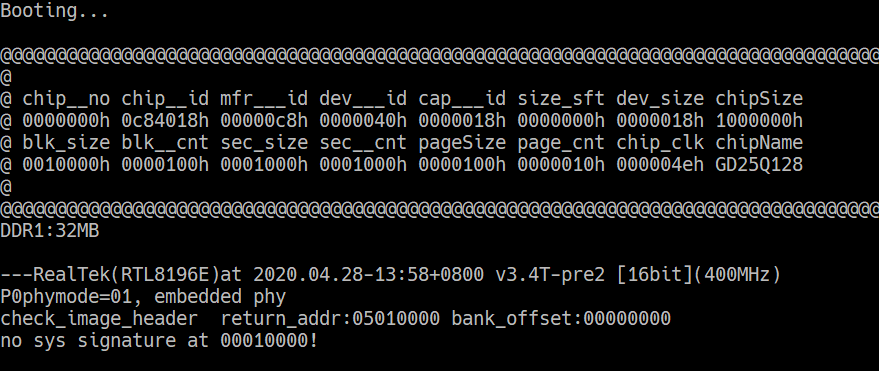
Connect the 3.3v to the gateway and start pressing ESC, you should see a prompt like this:
Retrieving the KEK (Encryption Key)
- Run the following commands in the terminal:
FLR 80000000 401802 16
DW 80000000 4
Save the output of these commands, it should be something like:
80000000: 743B5638 6872576B 47694E69 233C2778
Retrieving the AUSKEY
- Run the following commands in the terminal:
FLR 80000000 402002 32
DW 80000000 8
Save the output of these commands, it should be something like:
80000000: 110AAC2E CC412394 5387DC8C C98550E0
80000010: 7E64CE90 5795D7A9 4BA6FF51 8C2908E7
Decoding the root password
Download the Python script from Paul’s Github here: lidl_auskey_decode.py
Run the script and input the output from the commands you ran above (making sure to INCLUDE the 80000000: and 80000010:)
The script should then print your gateway’s root password.
Customise running software on the gateway
This section must be run on Linux or WSL (Or any Bash like shell)
- SSH into your gateway with the username
rootand the password you decoded earlier, the SSH server will be running on port2333and run the followingif [ ! -f /tuya/ssh_monitor.original.sh ]; then cp /tuya/ssh_monitor.sh /tuya/ssh_monitor.original.sh; fi echo "#!/bin/sh" >/tuya/ssh_monitor.sh reboot -
The SSH port of the gateway will now be running on the standard 22 instead of 2333
-
Download the serialgateway.bin from Paul’s website here: serialgateway.bin
- Use cat and ssh to upload this file to the gateway:
cat serialgateway.bin | ssh root@[gateway_ip] "cat >/tuya/serialgateway"
-
Connect to your gateway with ssh with the username
rootand with the password you decoded earlier -
Run the following on the Gateway:
if [ ! -f /tuya/tuya_start.original.sh ]; then cp /tuya/tuya_start.sh /tuya/tuya_start.original.sh; fi
cat >/tuya/tuya_start.sh <<EOF
#!/bin/sh
/tuya/serialgateway &
EOF
chmod 755 /tuya/serialgateway
reboot
Upgrade the EZSP Version to 6.7.8.0
This section must be run on Linux or WSL (Or any Bash like shell)
- Download the firmware_upgrade.sh script from Github here: firmware_upgrade.sh and the sx binary as well as the newer EZSP firmware from here: NCP_UHW_MG1B232_678_PA0-PA1-PB11_PA5-PA4.gbl
- Make sure the script is executable with
chmod +x ./firmware_upgrade.sh - Run the
firmware_upgrade.shscript like this:./firmware_upgrade.sh [gateway_ip] 22 V7 NCP_UHW_MG1B232_678_PA0-PA1-PB11_PA5-PA4.gbl- You may be prompted for the root password several times. - Reboot the gateway
For Home Assistant (ZHA)
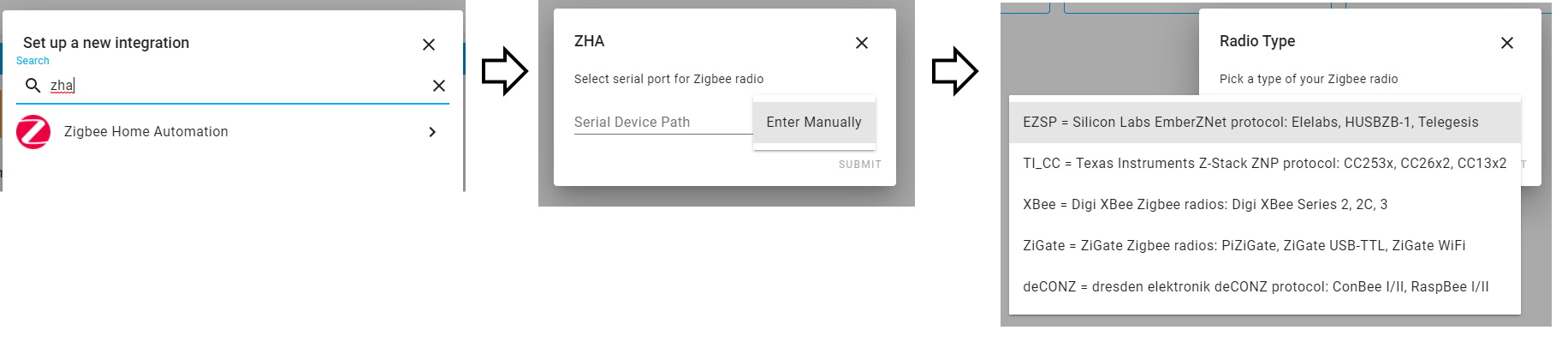
In Home Assistant (requires version 0.113+) go to Configuration - Integrations, click the + icon, search for ZHA integration and select it.
- choose “Enter Manually” for serial port
- for Radio Type choose “EZSP”
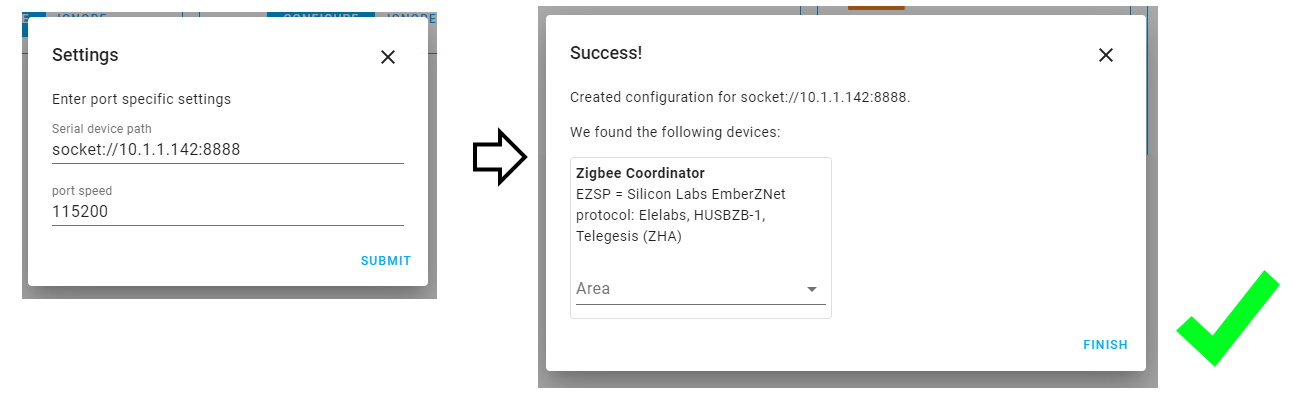
- under Serial device path enter
socket://[gateway_ip]:8888replacing[gateway_ip]with its IP address. Do not use hostnames.- if you changed the port number use yours
- set port speed to “115200”
- when the Gateway is discovered you will get a confirmation message